Cyber Intelligence Solution
The Cyber Intelligence Solution offers comprehensive protection against evolving cyber threats through advanced analytics and real-time monitoring. Designed to identify vulnerabilities and detect anomalies, this system empowers organizations to proactively safeguard their digital assets. With features such as threat intelligence integration, incident response support, and detailed reporting, our solution enables informed decision-making and enhances overall cybersecurity posture. Stay one step ahead of potential threats with a robust solution tailored to protect your critical information and infrastructure.
Open Source Intelligence (OSINT)
Open Source Intelligence (OSINT) provides a platform to accumulate and analyze information from multiple publicly available sources on the world wide web. It initiates relevant intelligence leads for performing open source intelligence and supports a wide spectrum of languages and topics available on the internet. It gathers information available in the public domain from Facebook, Twitter, YouTube, Google Plus, and many more. It is primarily used in national security, law enforcement, and business intelligence functions and is of value to analysts who use non-sensitive intelligence in answering classified, unclassified, or proprietary intelligence requirements across the previous intelligence disciplines.
Voice Analysis System (VAS)
Voice Analysis System (VAS) is a speech intelligence system, that performs comparison of biometric of voices for Speaker and Language recognition purpose.
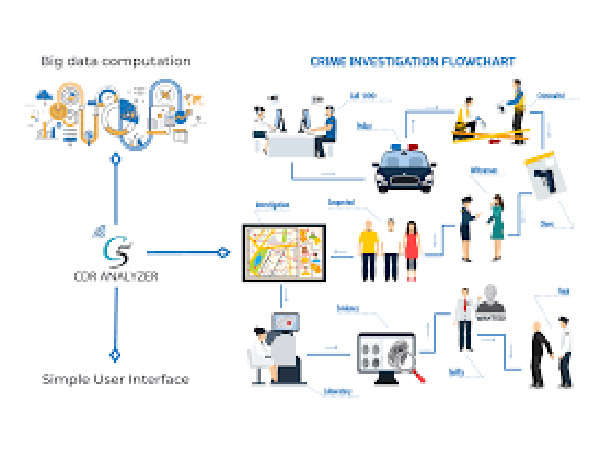
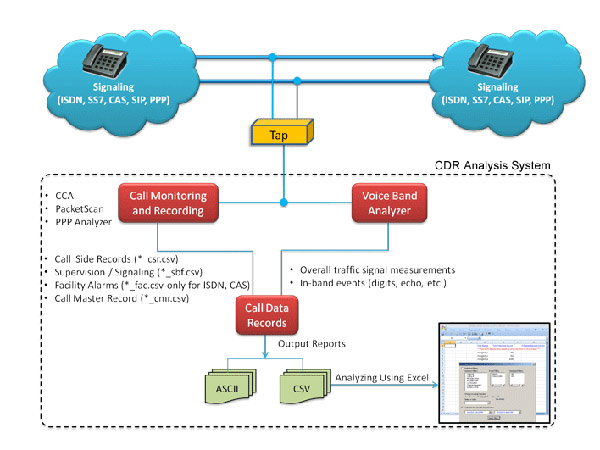
CDR Analysis System
CDR Analysis System capable for intelligent analysis and automated processing of large volumes of CDR (Call Detail Record) from any telecom service provider. It can import and analyze CDR, Tower/BTS Dump, Subscriber Details (SDR) and generates a wide range of reports of frequency statistics including service provider details.
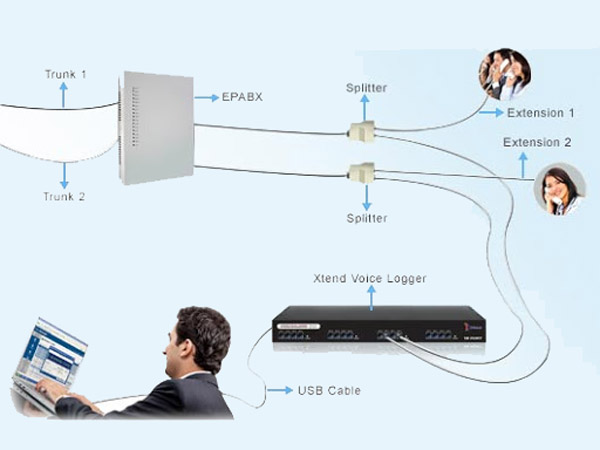
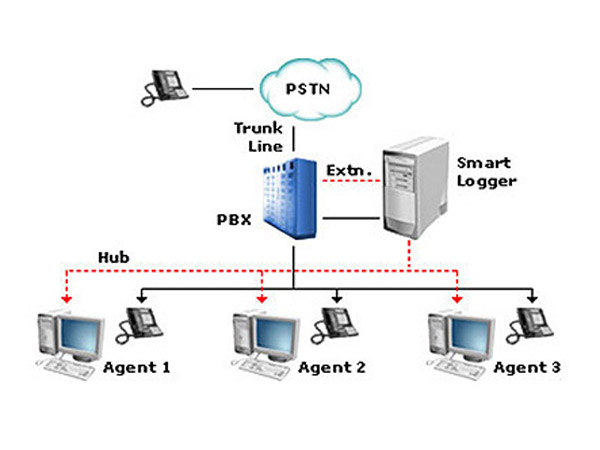
Voice Logger System
Voice Logger System is a performs live-listening and recording of voice calls from various telephony sources such as GSM, PSTN, CDMA networks, etc. It also provides comprehensive user-defined search and replay capabilities based on Date, Time, Duration, Calling/Called Number, etc.
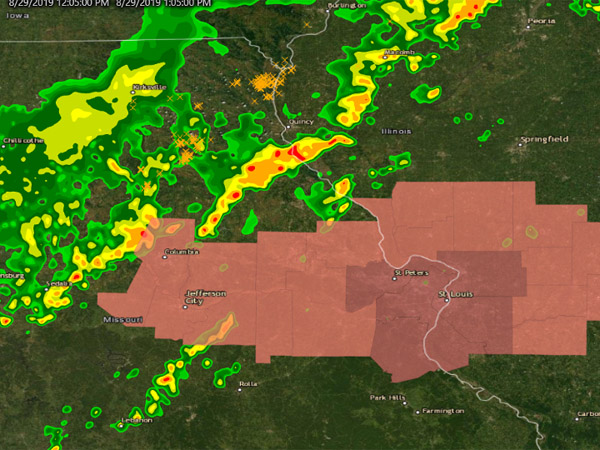
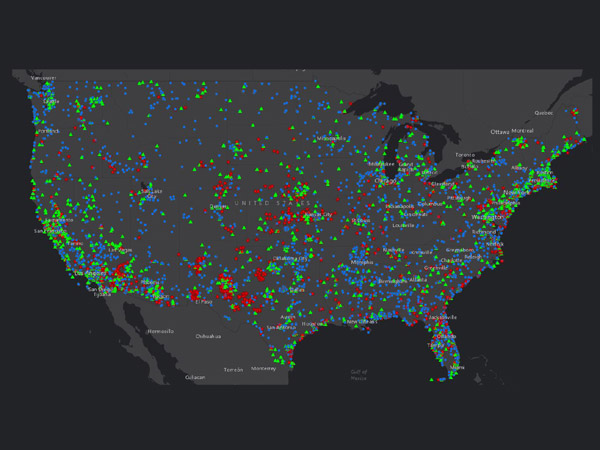
Geographic Analysis System
Geographic Analysis is a data mining methodology that utilizes location attributes to create a geographical representation of data.
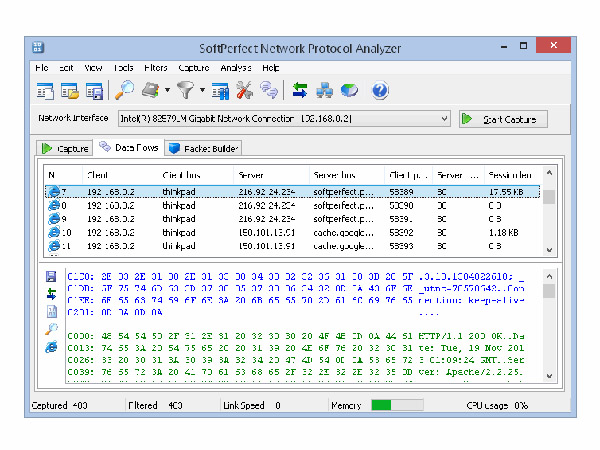
IP Protocol Analyzer
IP Protocol Analyzer provides a quick analysis of what exists in the fiber. It helps with analyzing and providing information based on total bytes and total packets.
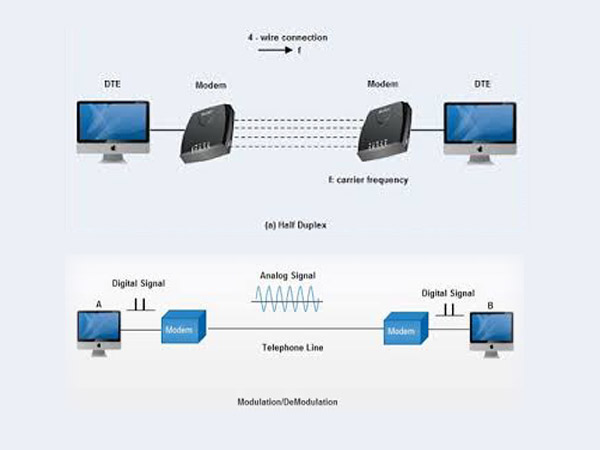
FAX and Modem Demodulator
Fax and Modem Demodulator is designed to perform interception of Fax and Modem data message by extraction of binary data exchanged by two modems during communication.
Visual Link Analysis (VLA)
Visual Link Analysis (VLA) is a high performance advance analytical tool that helps in converting communication records to visual data display multi-level hierarchical relationships.
Cyber Threat Intelligence - CTI
Threat intelligence, also known as cyber threat intelligence (CTI), is information gathered from a range of sources about current or potential attacks against an organization. The information is analyzed, refined and organized and then used to minimize and mitigate cybersecurity risks.
The main purpose of threat intelligence is to show organizations the various risks they face from external threats, such as zero-day threats and advanced persistent threats (APTs). Threat intelligence includes in-depth information and context about specific threats, such as who is attacking, their capabilities and motivation, and the indicators of compromise (IOCs). With this information, organizations can make informed decisions about how to defend against the most damaging attacks.
Why is Cyber threat intelligence important?
In a military, business or security context, intelligence is information that provides an organization with decision support and possibly a strategic advantage. Threat intelligence is a part of a bigger security intelligence strategy. It includes information related to protecting an organization from external and inside threats, as well as the processes, policies and tools used to gather and analyze that information.
Threat intelligence provides better insight into the threat landscape and threat actors, along with their latest tactics, techniques and procedures. It enables organizations to be proactive in configuring its security controls to detect and prevent advanced attacks and zero-day threats. Many of these adjustments can be automated so security stays aligned with the latest intelligence in real time.
Meet Our Experts
- Address: Level 36, Menara Maxis, Kuala Lampur City Centre, 50088, Kuala Lampur, Malaysia
- Phone: +60 111 722 5835
- Email: [email protected] , [email protected]
Download Section
| Document Title | Download |
Video Section
| Video Title | Play |